Lately, I've been messing around with iSCSI quite a bit both as a storage technology and as a replacement for conventional disks in Workstations and Application Servers; I'd been using it for years as a way to keep user profiles out of the root of C:\Documents and Settings or C:\Users by using a GPO and a couple of logon/logoff scripts; the iSCSI mount being necessary for users who needed access to their .PST files (which are not supported/ recommended to be run over an SMB/SMB2 network share).
About a year ago, I started booting Operating Systems from iSCSI using iSCSI-enabled NICs; The first iSCSI Adapters were actually hardware SCSI HBAs with a full TCP/IP Network stack built onto the board; the Operating System saw a SCSI adapter, nothing more. More modern iSCSI NICs can support both iSCSI and Network Duties. These newer NICs are technically a type of CNA (Converged Network Adapter) which allows the adapter to do double duty: operating as both a storage pathway and as a regular network adapter. These new iSCSI adapters were leveraging an ACPI call to something called the iBFT; the iSCSI Boot File Table: a memory space in which could be written by a boot kernel, and subsequently read by a full Operating System kernel.
While relatively trouble-free it took a while for OSes to catch up. CentOS/RedHat/SuSE/Ubuntu Linux have had full support for this method of booting and installation for some time, Windows platforms have not had direct parity with Linux when it comes to Booting from iSCSI.
Windows Server 2003 R2 SP2 was the first Microsoft OS to be certified for an iBFT iSCSI boot...but it was imperfect: it supported booting just fine... it did not support installation of the OS via iSCSI. WinXP could be made to boot from iSCSI, but it was not supported (But it worked).
About 2006, etherboot.org (Marty Conner and Michael Brown) started looking at the possibility of leveraging iSCSI via a PXE-Booted Kernel... thus was born gPXE.
From 2007 to 2009, gPXE progressed to the point where it was being used by mainstream vendors to replace conventional PXE Code: vendors like Emulex, HP and LSI Logic were actively developing solutions using gPXE. The gPXE project caught the attention of H. Peter Anvin (lead developer of Syslinux) and PXE binaries were compiled to leverage gPXE.
In the Spring of 2010 a codefork was precipitated because of personality conflicts between the principal developers. gPXE essentially has languished for over a year with no real changes, while the code fork iPXE has had ever more features and contributions some of which are turning heads in quite a few disciplines - particularly as it relates to virtualization.
Which brings us to my project...
The Stateless, "Soft" Desktop computer. I deliberately picked a low power system; the next iteration of it will probably be a fire-breathing gaming system of some type, just for laughs.
The Goal: Install, Configure and Run a Workstation from a single network adapter with no local storage devices of any kind (No USB, Optical Media or other temporary storage).
This obviously cannot be done without a fair amount of infrastructure planning and setup ahead of time.
Minimum Requirements:
a. A Network.
b. A DHCP Server supporting PXE.
c. A TFTP Server.
d. A Webserver (or a Broadband Internet connection)
e. An iSCSI Target.
Optional: A Linux Compile Environment.
Subsequent posts will detail the buildout...
About a year ago, I started booting Operating Systems from iSCSI using iSCSI-enabled NICs; The first iSCSI Adapters were actually hardware SCSI HBAs with a full TCP/IP Network stack built onto the board; the Operating System saw a SCSI adapter, nothing more. More modern iSCSI NICs can support both iSCSI and Network Duties. These newer NICs are technically a type of CNA (Converged Network Adapter) which allows the adapter to do double duty: operating as both a storage pathway and as a regular network adapter. These new iSCSI adapters were leveraging an ACPI call to something called the iBFT; the iSCSI Boot File Table: a memory space in which could be written by a boot kernel, and subsequently read by a full Operating System kernel.
While relatively trouble-free it took a while for OSes to catch up. CentOS/RedHat/SuSE/Ubuntu Linux have had full support for this method of booting and installation for some time, Windows platforms have not had direct parity with Linux when it comes to Booting from iSCSI.
Windows Server 2003 R2 SP2 was the first Microsoft OS to be certified for an iBFT iSCSI boot...but it was imperfect: it supported booting just fine... it did not support installation of the OS via iSCSI. WinXP could be made to boot from iSCSI, but it was not supported (But it worked).
About 2006, etherboot.org (Marty Conner and Michael Brown) started looking at the possibility of leveraging iSCSI via a PXE-Booted Kernel... thus was born gPXE.
From 2007 to 2009, gPXE progressed to the point where it was being used by mainstream vendors to replace conventional PXE Code: vendors like Emulex, HP and LSI Logic were actively developing solutions using gPXE. The gPXE project caught the attention of H. Peter Anvin (lead developer of Syslinux) and PXE binaries were compiled to leverage gPXE.
In the Spring of 2010 a codefork was precipitated because of personality conflicts between the principal developers. gPXE essentially has languished for over a year with no real changes, while the code fork iPXE has had ever more features and contributions some of which are turning heads in quite a few disciplines - particularly as it relates to virtualization.
Which brings us to my project...
The Stateless, "Soft" Desktop computer. I deliberately picked a low power system; the next iteration of it will probably be a fire-breathing gaming system of some type, just for laughs.
The Goal: Install, Configure and Run a Workstation from a single network adapter with no local storage devices of any kind (No USB, Optical Media or other temporary storage).
This obviously cannot be done without a fair amount of infrastructure planning and setup ahead of time.
Minimum Requirements:
a. A Network.
b. A DHCP Server supporting PXE.
c. A TFTP Server.
d. A Webserver (or a Broadband Internet connection)
e. An iSCSI Target.
Optional: A Linux Compile Environment.
Subsequent posts will detail the buildout...

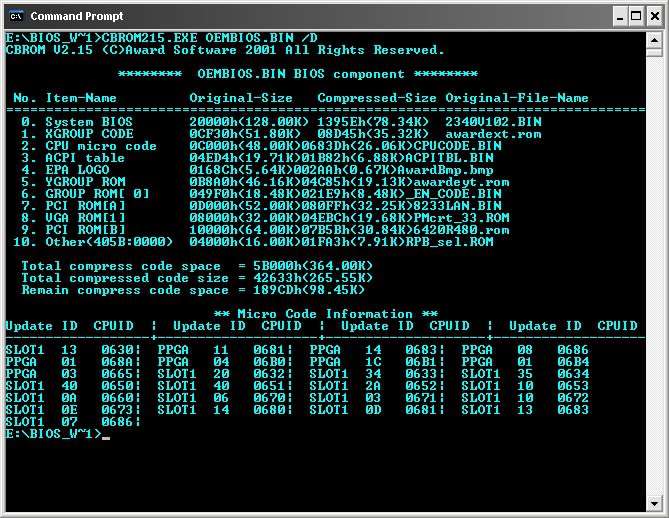
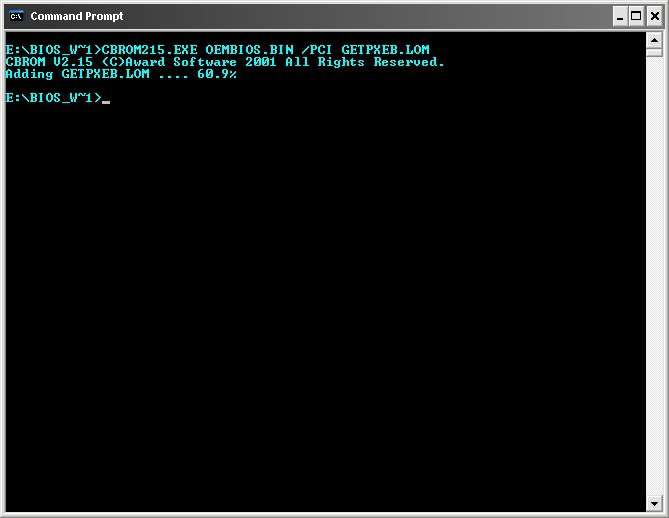



Comment